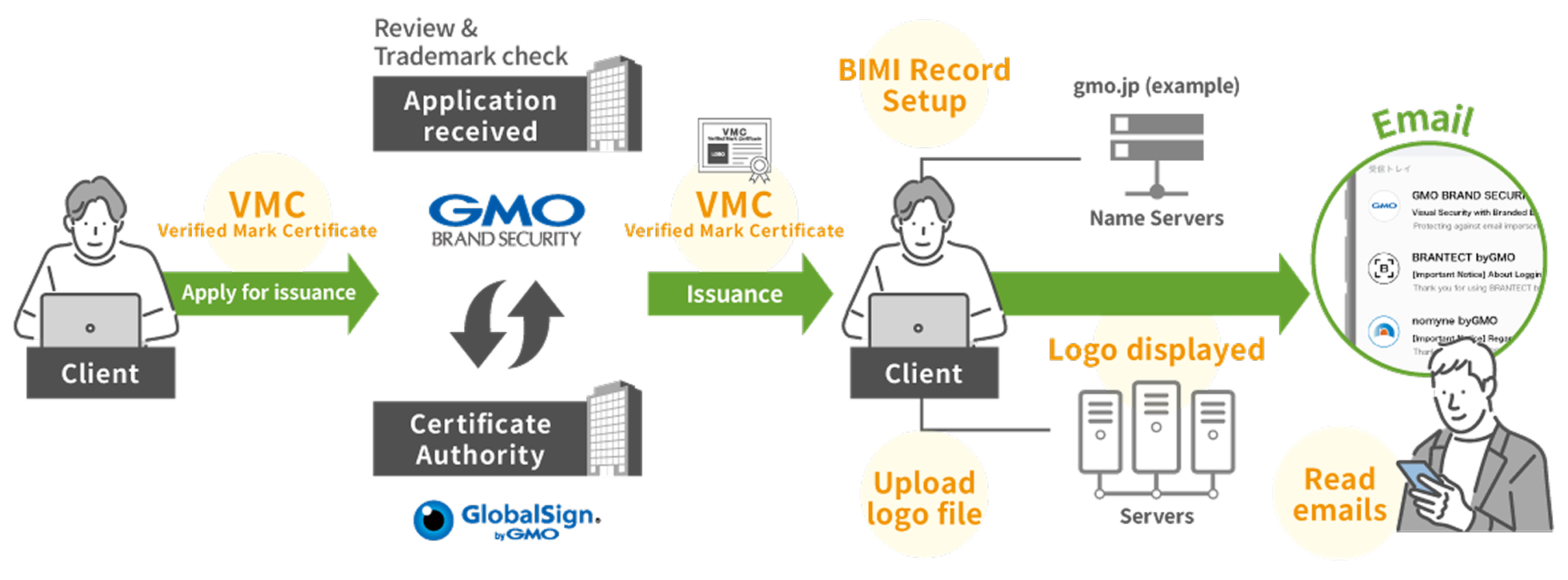
What are the requirements for using BIMI & VMC?
Step1Implement and Enforce DMARC
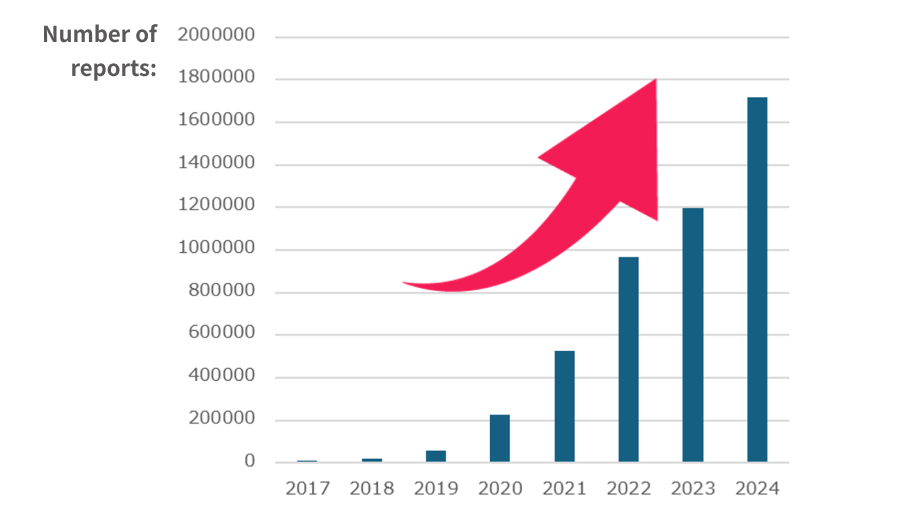
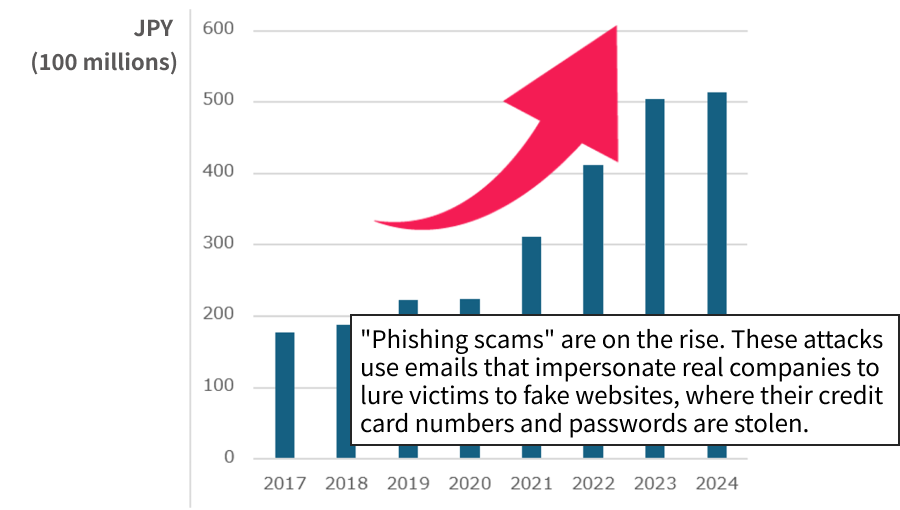
DMARC is an essential protocol that protects your domain from being used in phishing and spoofing attacks.
While many domains now have a DMARC policy of p=none to meet Google's guidelines, BIMI requires a stricter enforcement level. To display your logo, you must set your policy to either p=quarantine or p=reject.
IMPORTANT: Before you enforce a quarantine or reject policy, you must analyze your DMARC reports. This analysis is vital to ensure your valid emails don't get blocked and to avoid disrupting your email delivery.

Step2Register Your Brand Logo as a Trademark
The brand logo displayed in emails must be a registered trademark.
Your trademark needs to be registered with the intellectual property office of a country or region that is a member of the World Intellectual Property Organization (WIPO). The specific trademark class or the designated goods and services do not affect eligibility.

Step3Submit Your VMC Application
To complete your application for a Verified Mark Certificate (VMC), you will need:
Your Domain: The email domain you wish to certify.
Trademark Details: Information about your registered trademark. If you are a licensee, a letter of authorization from the trademark holder is required.
SVG Logo File: A logo file in the specific SVG Tiny 1.2 format. (Refer to the specifications here: https://support.google.com/a/answer/10911027?hl=en)
Proof of Organization: Official documents to prove your organization's legal status, such as articles of incorporation or a business license. The main types of documents are listed below.
- VMC Application Form
- User Agreement Form
- Certificate of Employment for the Authorized Signer
→ FAQ content is available in Japanese only. Please contact us for English support.

Check if your company logo is ready for BIMI.
SVG Logo Checker
Free : up to 10 checks per day
Version 1.0.0 – English Edition in Development
To check other settings (SPF, DMARC, BIMI), please use GMO Spoofing ZERO.


Step4Vetting and Verification
The VMC vetting process is comprehensive, combining the strict checks of an EV SSL certificate with dedicated trademark validation.
1. Domain validation
Confirms you are the legitimate user of the domain.
Performed either by approving a verification email sent to a public contact address for the domain, or by adding a specific token string provided by the CA to the domain’s DNS.
2. Existence/operational validation of the organization
Verifies that the organization and its authorized representatives actually exist and that the service is operated in reality.
Uses objective documents (e.g., company registration) and may include phone calls or in-person interviews to confirm operational substance and authority.
3. Trademark validation
Confirms the brand logo (SVG file) and the trademark registration status.
The trademark must be registered in a country/region that is a member of WIPO. Trademark class or designated goods/services do not matter, but the registered mark must match the brand logo.
If the logo differs from the registered mark (for example, if only a word mark is registered), a trademark application covering the logo may be required.

Step5Issuance of the Verified Mark Certificate (VMC)
The Certificate Authority (CA) will issue the Verified Mark Certificate (VMC) in PEM file format.
A PEM (Privacy Enhanced Mail) file is a standard format used to store cryptographic items such as digital certificates and private keys, primarily for encryption and authentication purposes.

Step6Final BIMI Configuration
The final configuration for BIMI involves the following two steps:
Upload the PEM File and SVG Logo
Create the BIMI DNS Record
1. Upload the PEM File and SVG Logo Upload your PEM file and your brand logo (in SVG format) to a publicly accessible location on your web server. It is required that these files are available at static URLs.
Example:
https://www.your-domain.com/bimi/vmc/certificate.pem
https://www.your-domain.com/bimi/logo/brand_logo.svg
2. Create the BIMI record in your DNS as follows.
→ FAQ content is available in Japanese only. Please contact us for English support.
By utilizing BIMI and VMC, users can engage with email with greater confidence. In turn, this enables companies to significantly enhance their brand's trustworthiness.